The geopolitical conflicts in the Middle East have deepened over the last few years. The crisis is taking many forms, and the conflict in cyberspace is intensifying as different sides try to shift the struggle in their favor by exploiting cyber intelligence and distorting news.
The Global Research and Analysis Team (GReAT) at Kaspersky Lab has uncovered new targeted attacks in the Middle East. Native Arabic-speaking cybercriminals have built advanced methods and tools to deliver, hide and operate malware that they have also developed themselves. This malware was originally discovered during an investigation of one of the attacks in the Middle East.
The Desert Falcons cybercriminals are native Arabic speakers; and it is believed to be the first known Arab group to develop and run a full cyber espionage operation. Desert Falcons began its operations in 2011, with the first infections taking place in 2013. The group became very active in late 2014/early 2015.
The Desert Falcons comprises around 30 members working in three teams and operating mainly out of Palestine, Egypt and Turkey.
The Desert Falcons make use of different tools and techniques to Deliver, Infect, Spy on and Manage their victims. Below we outline each of the methods involved and how they were carefully used to operate the cyber espionage activities. They are grouped into three sections as follows:
- Deceive and Infect
- Infiltrate and Spy
- Track and Control
Another technique used by the cybercriminals is to send a rar file that extracts to multiple files and offers an appealing shortcut in the form of a small, innocent-looking icon. In this case the victim does not need to double-click an executable file, the shortcut is enough to run a whole command to extract, setup and run the malware.
Desert Falcons use victims’ trust in social networking forums plus their curiosity about latest political news in the #MiddleEast
Tweet
Social Engineering and Backdoors
The Desert Falcons team is among to the first to run targeted attacks through Facebook chat. The attackers created authentic Facebook accounts and then interacted with chosen victims through common Facebook pages until they had gained their trust. Then they sent them Trojan files in the chat hidden as an image or similar.
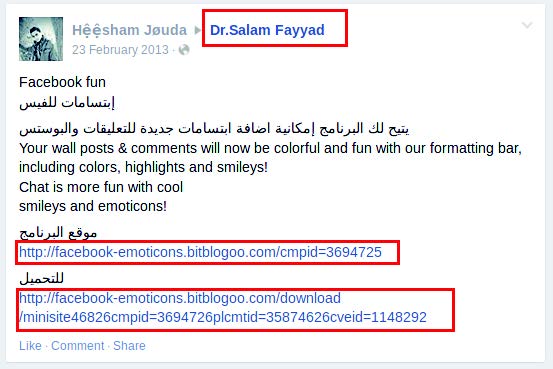
Facebook attacks targeted at generic activists and political followers (mass infection) For wider infections, especially among activists and political figures, different social engineering techniques were used. These included Facebook posts and redirects to fake pages with political content. We were able to identify suspect Facebook posts on popular activist pages,
with links to domains or malware downloads used by Falcons. Below are a few examples:
Posts made from compromised or fake accounts on political pages; Dr Salam Fayyad is a former prime minister of the state of Palestine.
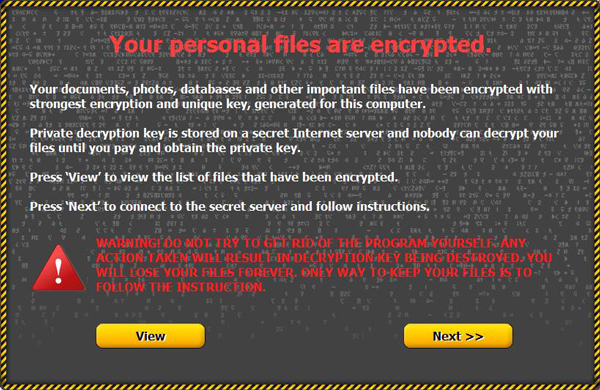
The Desert Falcons depend on two different backdoors to spy on victims. Both backdoors
are homemade and are under continuous development. We were able to identify and collect more than 100 malware samples used by the Desert Falcons.
Once they have infected the victim’s computer, attackers have full access and control, and they usually proceed as follows:
- New victims are categorized into groups before being infected (e.g. A001, A002, and so on)
- One of the cybercriminals is appointed to each new victim after infection
- A complete list of all files (especially XLS, DOC, JPG and WAV) is retrieved from the victim’s machine
- The cybercriminal browses and collects any interesting pictures and files
- The cybercriminal also collects chats and screenshots
- Depending on the importance of the victim, the surveillance is then either intensified or dropped
#DesertFalcons Main campaign targeted government, military, and media organisations in #Palestine, #Jordan, and #Gulf states. #FalconsAPT
— Kaspersky Lab ME (@KasperskyME) February 18, 2015
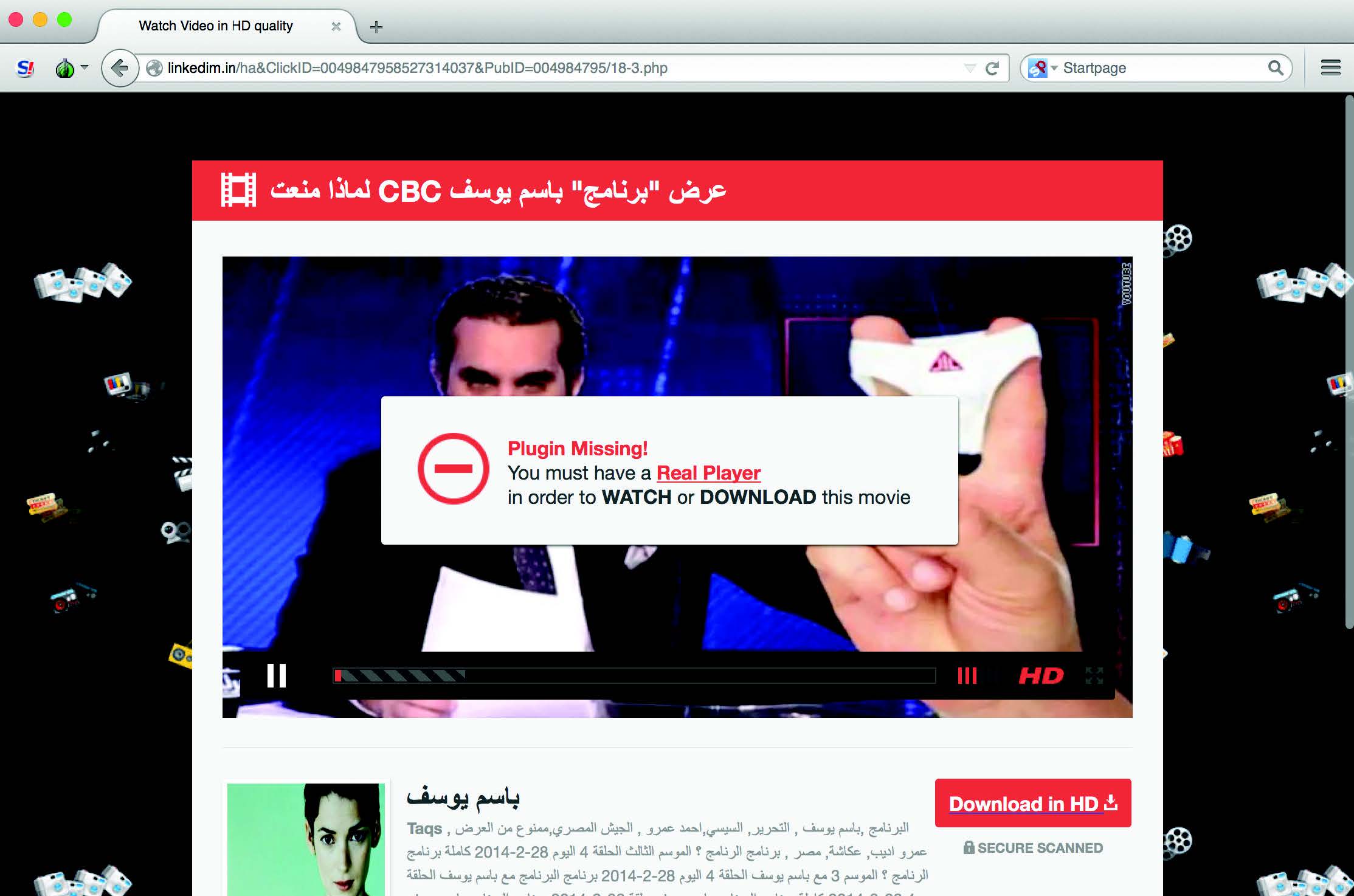
The fake RealPlayer plugin trick
In this case political social engineering was used to deliver malware as a “plugin” for the “banned video” of a famous political show in Egypt hosted by the satirist Bassem Youssef. The page was hosted on the following domain: www.linkedim.in, chosen to resemble the popular LinkedIn social networking site.
The Desert Falcons’ operation can be divided into three different campaigns, each operated from a different C&C/IP, targeting different types of victims and operated mostly by different team members.
The campaigns can be classified by the type and version of malware and the type of victims targeted:
- Campaign 1: Active in Palestine, Egypt, Jordan and the Gulf states (KSA, UAE and Qatar)
- Campaign 2: Active in Israel
- Campaign 3: Active in Egypt
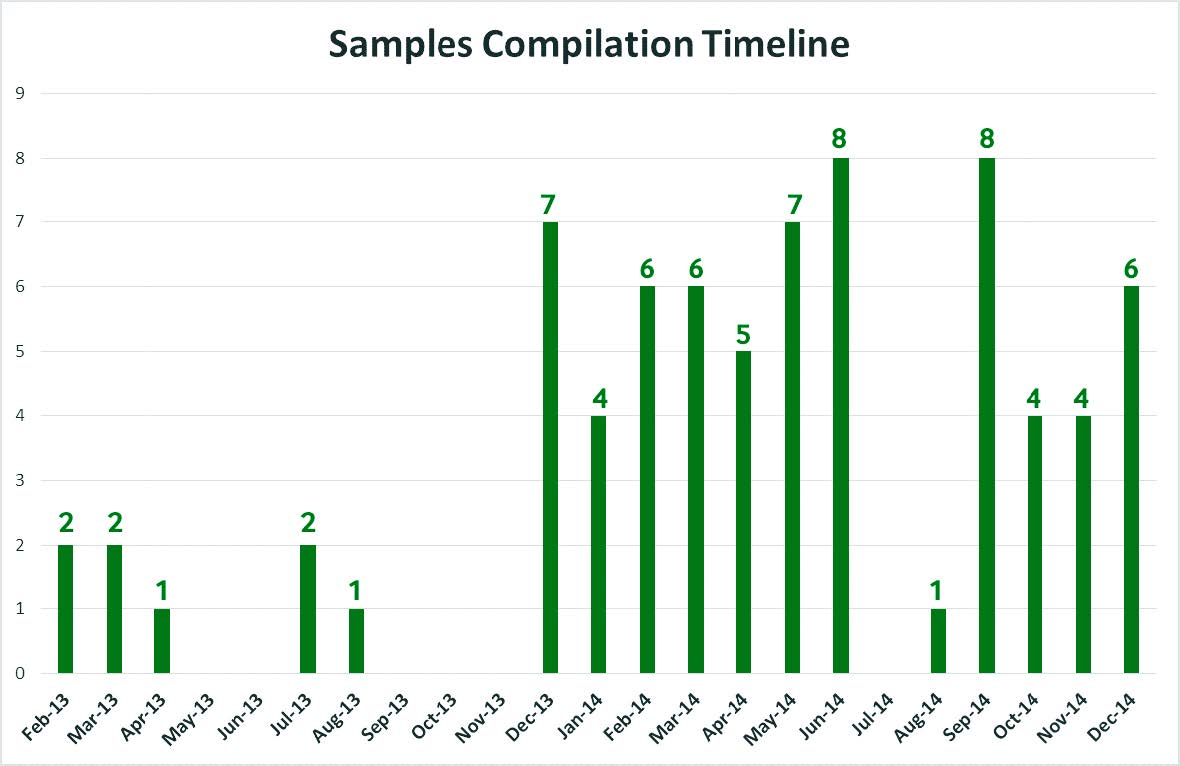
Compilation timeline for samples
The malware files compilation timeline for the collected samples clearly shows the Falcons’ activity and operations, which started in 2013 and increased dramatically in 2014.
This is just an alert for the poor cyber security situation in the region. Banks, Media outlets, Governments and Military entities in different countries all fell prey to the Desert Falcons’ attacks.
Falcons’ threat actors are determined, active and have good technical knowledge. We expect their operations to carry on developing more Trojans and using more advanced techniques. With enough funding, they might be able to acquire or develop exploits that would increase the efficiency of their attacks.
Desert Falcons is just one example of the rise of cybercrime in a geopolitically troubled region that will motivate other threat actors or states to leverage cyber attacks for political or criminal goals.
Kaspersky Lab clients are protected from infection, with the malware files and domains used in the targeted attacks detected and blocked.
To read the detailed security report:
https://securelist.com/blog/research/68817/the-desert-falcons-targeted-attacks/
 desert falcons
desert falcons

 Tips
Tips